Troubleshooting Cloudflare 5XX errors
When troubleshooting most 5XX errors, the correct course of action is to first contact your hosting provider or site administrator to troubleshoot and gather data.
When contacting your hosting provider, give them the following information:
- Specific 5XX error code and message.
- Time and timezone the 5XX error occurred.
- URL that resulted in the HTTP 5XX error (for example:
https://www.example.com/images/icons/image1.png).
The error cause is not always found in the origin server error logs. Check logs of all load balancers, caches, proxies, or firewalls between Cloudflare and the origin web server.
Additional details to provide to your hosting provider or site administrator are listed within each error description below. Cloudflare Custom Error Pages change the appearance of default error pages discussed in this article.
Error Analytics per domain are available within Zone Analytics. Error Analytics allows insight into overall errors by HTTP error code and provides the URLs, source IP addresses, and Cloudflare data centers needed to diagnose and resolve the issue. Error Analytics are based on a 1% traffic sample.
To view Error Analytics:
- Log in to the Cloudflare dashboard.
- Click the appropriate Cloudflare account for your site, then pick the domain.
- Next, click the Analytics & Logs app icon.
- Click Add filter, select Edge status code or Origin status code and choose any 5xx error code that you want to diagnose.
Error 500 generally indicates an issue with your origin web server. Error establishing database connection is a common HTTP 500 error message generated by your origin web server. Contact your hosting provider to resolve.
Resolution
Provide details to your hosting provider to assist troubleshooting the issue.
However, if the 500 error contains “cloudflare” or “cloudflare-nginx” in the HTML response body, provide Cloudflare support with the following information:
- Your domain name
- The time and timezone of the 500 error occurrence
- The output of
www.example.com/cdn-cgi/tracefrom the browser where the 500 error was observed (replacewww.example.comwith your actual domain and hostname)
An HTTP 502 or 504 error occurs when Cloudflare is unable to establish contact with your origin web server.
There are two possible causes:
- (Most common cause) 502/504 from your origin web server
- 502/504 from Cloudflare
Cloudflare returns an Cloudflare-branded HTTP 502 or 504 error when your origin web server responds with a standard HTTP 502 bad gateway or 504 gateway timeout error:
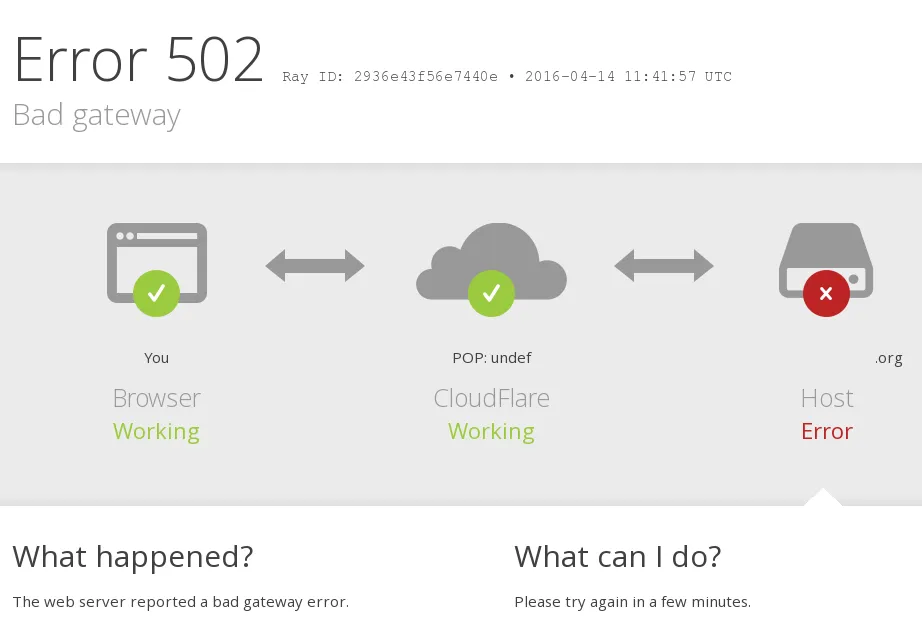
Resolution
Contact your hosting provider to troubleshoot these common causes at your origin web server:
- Ensure the origin server responds to requests for the hostname and domain within the visitor’s URL that generated the 502 or 504 error.
- Investigate excessive server loads, crashes, or network failures.
- Identify applications or services that timed out or were blocked.
A 502 or 504 error originating from Cloudflare appears as follows:
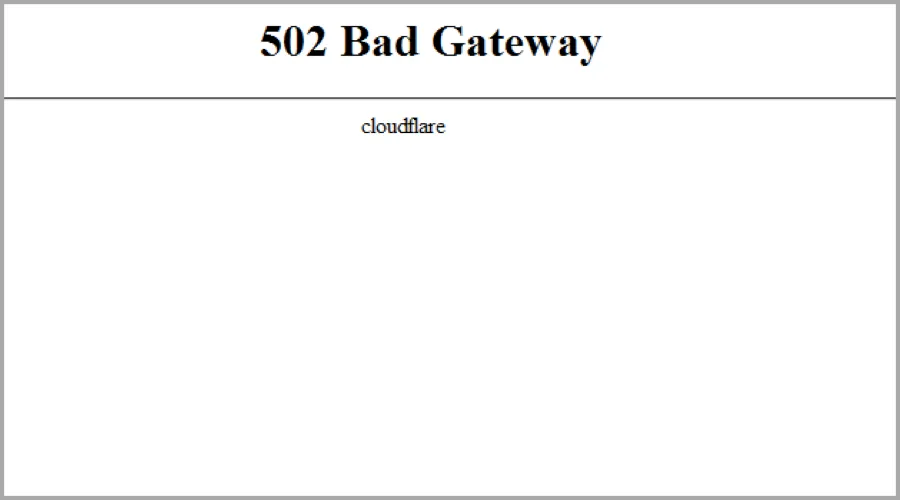
If the error does not mention cloudflare, contact your hosting provider for assistance on 502/504 errors from your origin.
This error can be returned in case of a compression issue at the origin, for example the origin server is serving gzip encoded compressed content but is not updating the content-length header, or the origin is serving broken gzip compressed content.
You can try to disable compression at your origin to confirm if this is the root cause of the errors.
Otherwise, under certain conditions it is possible a given Data Center observes a sudden increase of traffic. In these cases our automated processes will move traffic away from such location to a different Data Center making sure there is no impact for our customers. These traffic adjustments are mostly seamless and take only a few seconds. Still, it is possible that during this automated process some clients observe added latency and HTTP 502 errors. You can find more information about our automated traffic management tools in this blogpost ↗.
Resolution
If you still need our Support team to help you investigate further, please provide these required details to Cloudflare Support to avoid delays processing your inquiry:
- Time and timezone the issue occurred.
- URL that resulted in the HTTP 502 or 504 response (for example:
https://www.example.com/images/icons/image1.png). - Output from browsing to
<YOUR_DOMAIN>/cdn-cgi/trace.
HTTP error 503 occurs when your origin web server is overloaded. There are two possible causes discernible by error message:
- Error doesn’t contain
cloudflareorcloudflare-nginxin the HTML response body.
Resolution: Contact your hosting provider to verify if they rate limit requests to your origin web server.
- Error contains
cloudflareorcloudflare-nginxin the HTML response body.
Resolution: A connectivity issue occurred in a Cloudflare data center. Provide Cloudflare support with the following information:
- Your domain name
- The time and timezone of the 503 error occurrence
- The output of
www.example.com/cdn-cgi/tracefrom the browser where the 503 error was observed (replacewww.example.comwith your actual domain and hostname)
Error 520 occurs when the origin server returns an empty, unknown, or unexpected response to Cloudflare.
Resolution
Contact your hosting provider or site administrator and request a review of your origin web server error logs for crashes and to check for these common causes:
- Origin web server application crashes
- Cloudflare IPs ↗ not allowed at your origin
- Headers exceeding 16 KB (typically due to too many cookies)
- An empty response from the origin web server that lacks an HTTP status code or response body
- Missing response headers or origin web server not returning proper HTTP error responses ↗.
If HTTP/2 is enabled at your origin web server, please check and make sure HTTP/2 is correctly configured. Cloudflare connects to servers who announce support of HTTP/2 connections via ALPN ↗. If the origin web server accepts the HTTP/2 connection but then doesn’t respect or support the protocol, an HTTP Error 520 will be returned. You can disable the HTTP/2 to Origin setting on the Cloudflare Dashboard under Speed -> Optimization -> Protocol Optimization and check your origin web server configuration further.
If 520 errors continue after contacting your hosting provider or site administrator, provide the following information to Cloudflare Support:
- Full URL(s) of the resource requested when the error occurred
- Cloudflare cf-ray from the 520 error message
- Output from
http://<YOUR_DOMAIN>/cdn-cgi/trace - Two HAR files:
- one with Cloudflare enabled on your website, and
- the other with Cloudflare temporarily disabled.
Error 521 occurs when the origin web server refuses connections from Cloudflare. Security solutions at your origin may block legitimate connections from certain Cloudflare IP addresses ↗.
The two most common causes of 521 errors are:
- Offlined origin web server application
- Blocked Cloudflare requests
Resolution
Contact your site administrator or hosting provider to eliminate these common causes:
- Ensure your origin web server is responsive
- Review origin web server error logs to identify web server application crashes or outages.
- Confirm Cloudflare IP addresses ↗ are not blocked or rate limited
- Allow all Cloudflare IP ranges ↗ in your origin web server’s firewall or other security software
- Confirm that — if you have your SSL/TLS mode set to Full or Full (Strict) — you have installed a Cloudflare Origin Certificate
- Find additional troubleshooting information on the Cloudflare Community ↗.
Error 522 occurs when Cloudflare times out contacting the origin web server. Two different timeouts cause HTTP error 522 depending on when they occur between Cloudflare and the origin web server:
- Before a connection is established, the origin web server does not return a SYN+ACK to Cloudflare within 15 seconds of Cloudflare sending a SYN.
- After a connection is established, the origin web server doesn’t acknowledge (ACK) Cloudflare’s resource request within 90 seconds.
Resolution
Contact your hosting provider to check the following common causes at your origin web server:
- (Most common cause) Cloudflare IP addresses ↗ are rate limited or blocked in .htaccess, iptables, or firewalls. Confirm your hosting provider allows Cloudflare IP addresses.
- An overloaded or offline origin web server drops incoming requests.
- Keepalives ↗ are disabled at the origin web server.
- The origin IP address in your Cloudflare DNS app does not match the IP address currently provisioned to your origin web server by your hosting provider.
- Packets were dropped at your origin web server.
If you are using Cloudflare Pages, verify that you have a custom domain set up and that your CNAME record is pointed to your custom Pages domain.
If none of the above leads to a resolution, request the following information from your hosting provider or site administrator before contacting Cloudflare support:
- An MTR or traceroute from your origin web server to a Cloudflare IP address ↗ that most commonly connected to your origin web server before the issue occurred. Identify a connecting Cloudflare IP recorded in the origin web server logs.
- Details from the hosting provider’s investigation such as pertinent logs or conversations with the hosting provider.
Error 523 occurs when Cloudflare cannot contact your origin web server. This typically occurs when a network device between Cloudflare and the origin web server doesn’t have a route to the origin’s IP address.
Resolution Contact your hosting provider to exclude the following common causes at your origin web server:
- Confirm the correct origin IP address is listed for A or AAAA records within your Cloudflare DNS app.
- Troubleshoot Internet routing issues between your origin and Cloudflare, or with the origin itself.
If none of the above leads to a resolution, request the following information from your hosting provider or site administrator:
- An MTR or traceroute from your origin web server to a Cloudflare IP address ↗ that most commonly connected to your origin web server before the issue occurred. Identify a connecting Cloudflare IP from the logs of the origin web server.
Error 524 usually indicates that Cloudflare successfully connected to the origin web server, but the origin did not provide an HTTP response before the default 100 second Proxy Read Timeout. This can happen if the origin server is taking too long because it has too much work to do - e.g. a large data query, or because the server is struggling for resources and cannot return any data in time.
Error 524 can also indicate that Cloudflare successfully connected to the origin web server to write data, but the write did not complete before the 30 second Proxy Write Timeout.
Resolution
Here are the options we’d suggest to work around this issue:
- Implement status polling of large HTTP processes to avoid hitting this error.
- Contact your hosting provider to exclude the following common causes at your origin web server:
- A long-running process on the origin web server.
- An overloaded origin web server.
- Enterprise customers can increase the 524 timeout up to 6,000 seconds using the Edit zone setting endpoint (
proxy_read_timeoutsetting). If your content can be cached, you may also choose to use a Cache Rule with theProxy Read Timeoutsetting selected instead in the Cloudflare Dashboard.
- If you regularly run HTTP requests that take over 100 seconds to complete (for example large data exports), move those processes behind a subdomain not proxied (grey clouded) in the Cloudflare DNS app.
525 errors indicate that the SSL handshake between Cloudflare and the origin web server failed. Error 525 occurs when these two conditions are true:
- The SSL handshake ↗ fails between Cloudflare and the origin web server, and
- Full or Full (Strict) SSL is set in the Overview tab of your Cloudflare SSL/TLS app.
Resolution
Contact your hosting provider to exclude the following common causes at your origin web server:
- No valid SSL certificate installed
- Port 443 (or other custom secure port) is not open
- No SNI support
- The cipher suites presented by Cloudflare to the origin do not match the cipher suites supported by the origin web server
Additional checks
- Check if you have a certificate installed on your origin server. You can check this article for more details on how to run some tests. In case you don’t have any certificate, you can create and install our free Cloudflare origin CA certificate. Using Origin CA certificates allows you to encrypt traffic between Cloudflare and your origin web server.
- Review the cipher suites your server is using to ensure they match what is supported by Cloudflare.
- Check your server’s error logs from the timestamps you see 525s to ensure there are errors that could be causing the connection to be reset during the SSL handshake.
Error 526 occurs when these two conditions are true:
- Cloudflare cannot validate the SSL certificate at your origin web server, and
- Full SSL (Strict) SSL is set in the Overview tab of your Cloudflare SSL/TLS app.
Resolution
Request your server administrator or hosting provider to review the origin web server’s SSL certificates and verify that:
- Certificate is not expired
- Certificate is not revoked
- Certificate is signed by a Certificate Authority ↗ (not self-signed)
- The requested or target domain name and hostname are in the certificate’s Common Name or Subject Alternative Name
- Your origin web server accepts connections over port SSL port 443
- Temporarily pause Cloudflare and visit https://www.sslshopper.com/ssl-checker.html#hostname=www.example.com ↗ (replace
www.example.comwith your hostname and domain) to verify no issues exists with the origin SSL certificate:
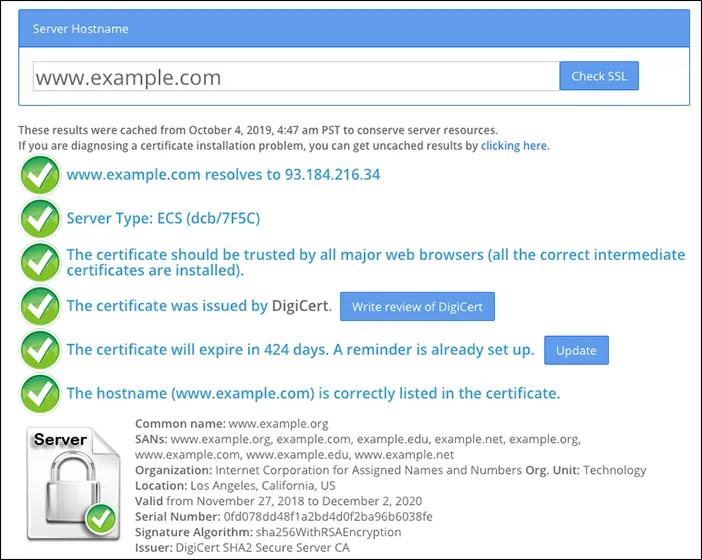
If the origin server uses a self-signed certificate, configure the domain to use Full SSL instead of Full SSL (Strict). Refer to recommended SSL settings for your origin.
When using Cloudflare Gateway, an HTTP Error 526 might be returned in the following cases:
-
An untrusted certificate is presented from the origin to Gateway. Gateway will consider a certificate is untrusted if any of these conditions are true:
- The server certificate issuer is unknown or is not trusted by the service.
- The server certificate is revoked and fails a CRL check.
- There is at least one expired certificate in the certificate chain for the server certificate.
- The common name on the certificate does not match the URL you are trying to reach.
- The common name on the certificate contains invalid characters (such as underscores). Gateway uses BoringSSL ↗ to validate certificates. Chrome’s validation logic ↗ allows non-RFC 1305 compliant certificates, which is why the website may load when you turn off WARP.
-
The connection from Gateway to the origin is insecure. Gateway does not trust origins which:
- Only offer insecure cipher suites (such as RC4, RC4-MD5, or 3DES). You can use the SSL Server Test tool ↗ to check which ciphers are supported by the origin.
- Do not support FIPS-compliant ciphers (if you have enabled FIPS compliance mode). In order to load the page, you can either disable FIPS mode or create a Do Not Inspect policy for this host (which has the effect of disabling FIPS compliance for this origin).
- Redirect all HTTPS requests to HTTP.
Workers subrequests to any hostname outside of your Cloudflare zone that is not proxied by Cloudflare are always made using the Full (strict) SSL mode, even when the Workers zone is configured otherwise.
As a result, a valid SSL certificate is required at the origin.
HTTP error 530 is returned with an accompanying 1XXX error displayed. Search for the specific 1XXX error for troubleshooting information.
Enabling Load Balancing in China will cause a 530 error.